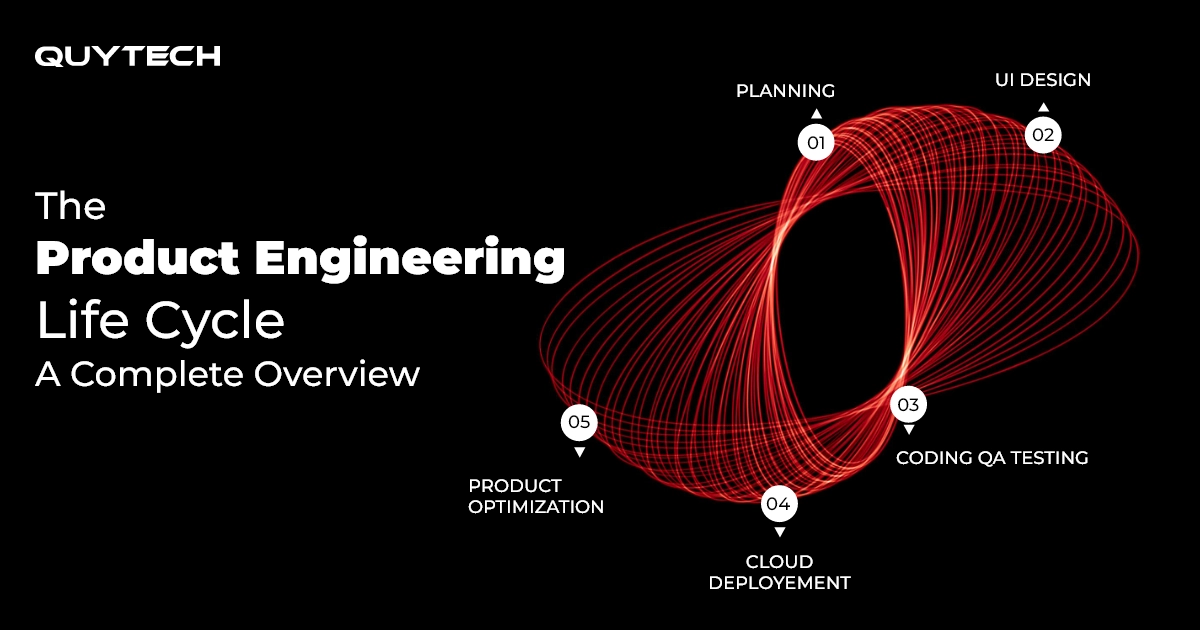
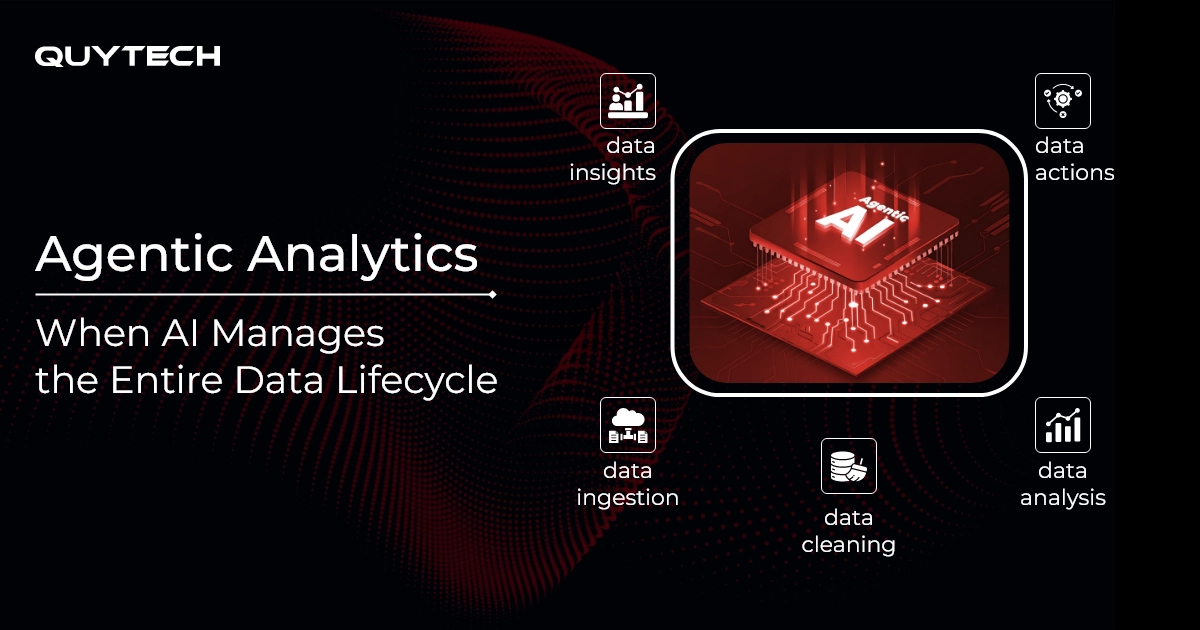
Quytech Partners with U.S.-Based AIiIA Consulting for Healthcare AI Innovation
Quytech announces a strategic partnership with the U.S.-based AIiIA Consulting, a strategy-led AI advisory firm that supports scaling organizations in making informed and responsible decisions […]